I was watching a lecture on computer security recently and came up to this website called shodan.io. Well apparently, I’m too late to the party, it is out there since 2009.
Before finding Shodan, I always assumed that gathering data about system security, needs some basic knowledge about what you are looking for and at least access to some scanners like Nmap, but now, it’s just a click away!
So what is the big deal?
As web developers, we use a lot of tools on our stack. And about 99.999% of the times, databases are vital parts of this stack. There are a variety of databases out there, designed for different use cases and scenarios, and of course, they vary on their security measures.
MongoDB, this cool little guy, which is designed as NOSQL database, and we can name it database for lazy people since it happens a lot to consider it as an option whenever we need a database just because it’s much easier to use, doesn’t provide that much of security out of the box! Actually, in older versions, its security measures (by default) are close to zero!
Well, to testify this, you can take a look at Shodan report on MongoDB product:
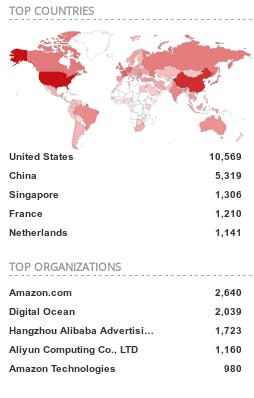
Sodan report on MongoDB product
I picked some IPs from the top of the given list, and logged in successfully without any problem! Full access to data. Just a matter of:
mongo --host x.x.x.x
The same scenario applies to Redis. Use a simple redis-cli -h x.x.x.x to access any server on that list.
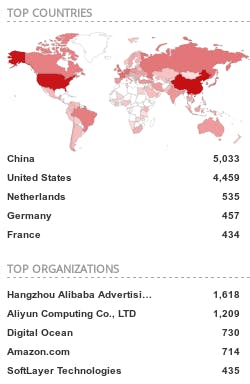
Shodan report on Redis product
So what should we do?
I’m not sure about all use cases out there, and how much this being naked in the wild is necessary, but I can assure you that it is much safer to put that damn database behind a firewall and restrict its open access just to yourself.
In versions greater than 3, Mongo suggests that binding to global access 0.0.0.0 is unnecessary and warns you. For Redis, you will face a horrible story about older versions bound to global access, yet still, newer versions are not that much safe to just reveal its access to the world!
Mongo provides an authentication system which is a good thing to have and will protect you from unwanted access. Actually, I suggest using it even if you are sure about your server’s safety. Not enabling it by default, is a gift to hackers out there:
NoSQL, or rather NoAuthentication, has been a huge gift to the hacker community. Just when I was worried that they’d finally patched all of the authentication bypass bugs in MySQL, new databases came into style that lack authentication by design.
You can protect your Redis servers using authentication system as well.
Not binding your database systems to global access and using an authentication system, will provide you a minimum required security. It’s totally fine. But surely it’s not enough. There are always new security bugs hidden somewhere that can provide security breaches to your stack.
Using a firewall will lower that risk. If you are using a Linux server and you are afraid of complicated firewall configurations, just use ufw. It’s easy and it’s great;
$ ufw default deny #Deny all incoming requests
$ ufw enable
Just like that you can reject any unnecessary access to your server and buy yourself some confidence. You can learn more about ufw here and tune it based on your needs (it’s super easy).
What about data on Shodan?
If you live in a country with a law that supports your good faith, you can try to find and warn the people responsible for those servers.
But if you are in a country with a law that allows vulnerable people to sue you without considering your faith, and startups/vendors are forbidding you from any kind of security check or report (Yes, such countries/startups/people exist, who still need time to learn about the value of security the hard way), the best thing you can do is to learn from this mistakes and teach others.
PS: Related discussion threads on Reddit and HackerNews.
